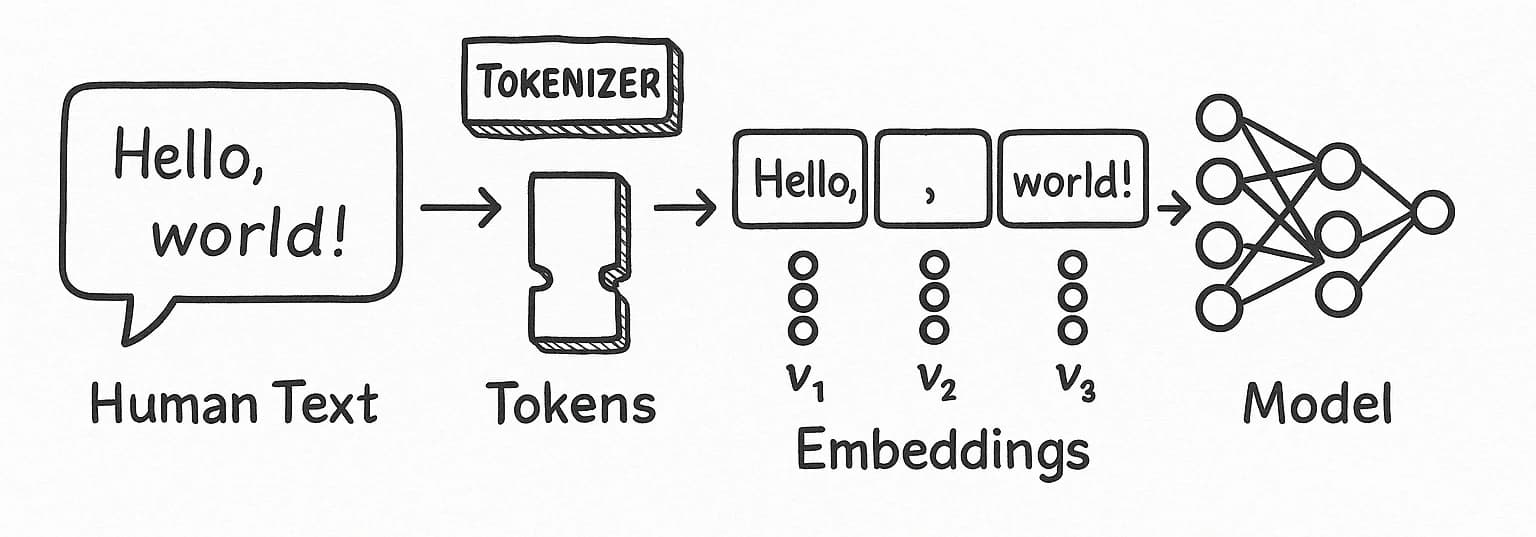
Cut Your LLM Token Bill in Half - How TOON Rewrites the Rules of JSON
Discover how TOON (Token-Oriented Object Notation) can reduce your LLM API costs by 30-60% through smarter data formatting designed specifically for AI applications.
Thoughts, tutorials, and insights on technology, development, and everything in between.

Discover how TOON (Token-Oriented Object Notation) can reduce your LLM API costs by 30-60% through smarter data formatting designed specifically for AI applications.

A deep technical yet approachable breakdown of how massive platforms check username availability instantly while ensuring accuracy at scale.

Understand the key differences between encoding, hashing, and encryption - including how they work, their use cases, and real-world examples.

A beginner-friendly explanation of how public and private keys work together to power encryption, digital signatures, and secure communication online.

This blog introduces the basics of Java Cryptography in plain English — covering encryption, decryption, hashing, and how they help secure applications.

A deep dive into Binary Search, covering its algorithm, implementation, variations, and real-world applications.